Continuous Threat Exposure Management (CTEM)
With certain organisations, one-off security assessments are no longer enough. Cybergen’s Continuous Threat Exposure Management (CTEM) service provides a proactive, ongoing approach to identifying, prioritising, and mitigating cyber risks across your entire digital environment.
By continuously monitoring your attack surface, simulating real-world threats, and aligning with business-critical assets, CTEM empowers your organisation to make smarter, faster security decisions, before attackers can exploit your weaknesses.
YOU CAN'T PROTECT WHAT YOU CAN'T SEE

CTEM is designed to continuously validate, prioritise, and remediate threats based on real-world risk and business impact. It includes five stages: scoping, discovery, prioritisation, validation, and mobilisation. CTEM is strategic, it's about managing how exposed your organisation is to real threats, and not just knowing what assets exist.
60%
of companies with CTEM reduce breach impact by up to 60%, due to faster detection and targeted remediation.
67%
of organisations say they lack continuous visibility into their attack surface, making it harder to prioritise and respond to emerging threats.
CTEM is a broader security framework that includes Attack Surface Management (ASM) but goes further.
Developed around Gartner’s model, CTEM is designed to continuously validate, prioritise, and remediate threats based on real-world risk and business impact. It includes five stages: scoping, discovery, prioritisation, validation, and mobilisation.
Limited Visibility
As IT infrastructure, SaaS adoption, cloud services, and shadow IT expand rapidly, maintaining clear visibility of your attack surface is becoming increasingly challenging.
Instant Threat Activation
From initial discovery to widespread exploitation, organisations now have less time than ever to detect and defend against vulnerabilities.
Constant Adversarial Evolution
Attackers are continuously evolving their tactics and techniques, but annual, quarterly, or even monthly cybersecurity testing fails to keep pace with this ever-changing threat landscape.
Unrealistic Testing
Traditional security testing no longer aligns with the reality of modern threats — constrained by limited time, narrow scope, and outdated approaches.
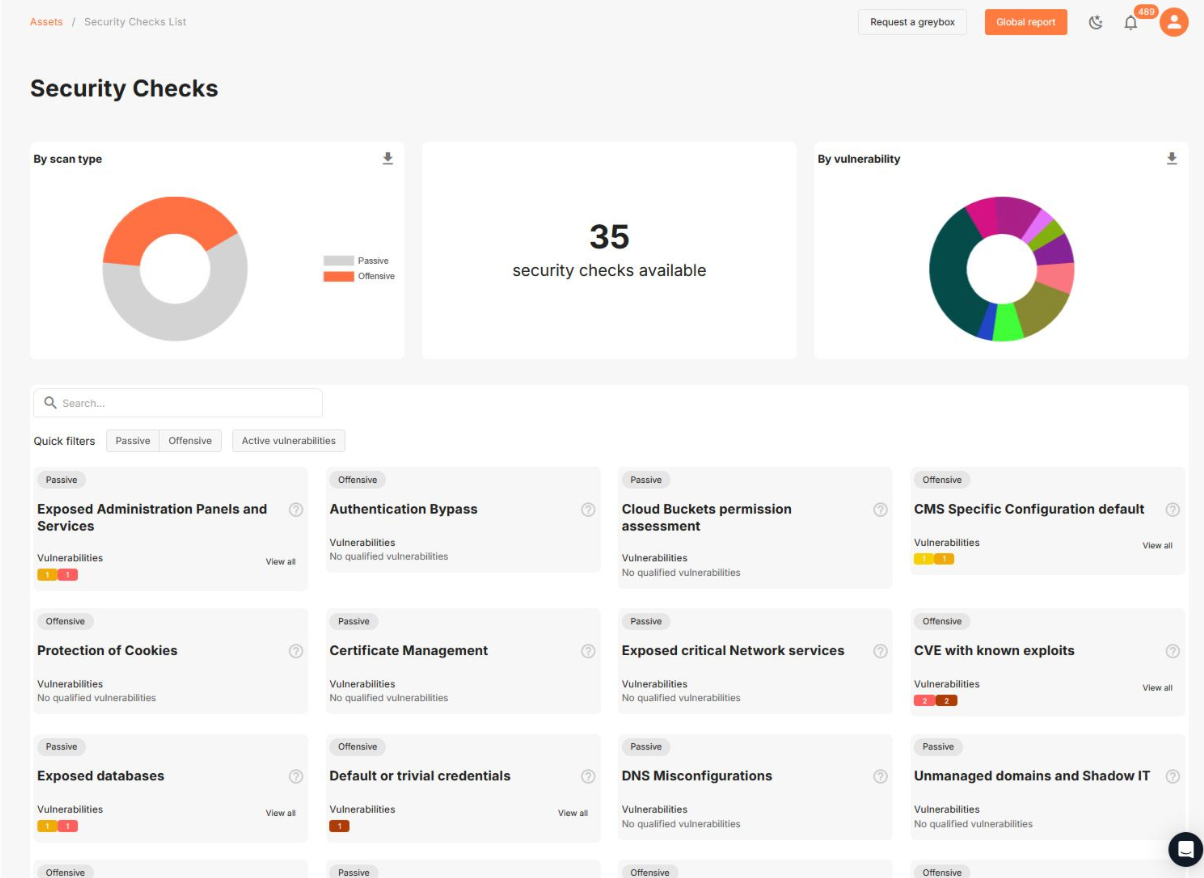
Identify Your Vulnerabilities
Identify all your vulnerabilities with automated pentesting:
- Known vulnerabilities, the referenced vulnerabilities (CVE) but also unreferenced ones
- Unknown vulnerabilities and weaknesses, based on well known standards: OWASP, PTES and OSSTMM
Get the same quality as a manual pentest but continuously, on perimeters of infinite size and consolidated in a centralised dashboard.
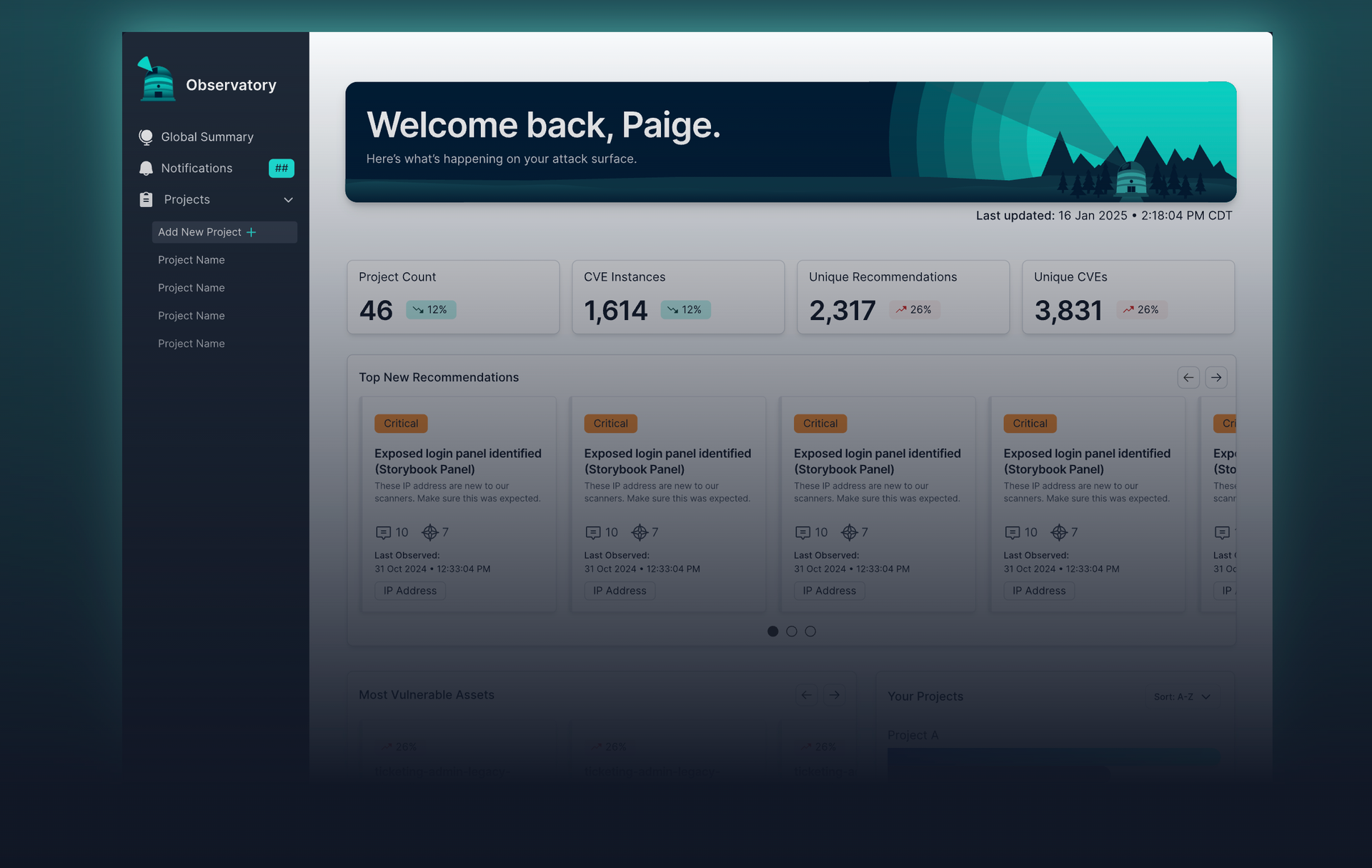
Why Do I Need Continuous Threat Exposure Management?
Your digital attack surface is constantly expanding and with it, your exposure to cyber threats. Traditional security measures are no longer enough to keep pace with how attackers operate. At Cybergen, we recommend adopting a Continuous Threat Exposure Management (CTEM) approach to proactively identify, validate, and reduce cyber risk across your entire environment.
Combing real-time visibility, attack surface management, and threat validation, giving you a clear view of what attackers can see and exploit. Unlike one-off assessments, CTEM is continuous, strategic, and aligned with business risk. It empowers security teams to prioritise what matters most and respond with speed and confidence, reducing your overall exposure and strengthening resilience.
Cyber Threats Evolve Faster Than Traditional Testing Can Keep Up
Attackers are constantly refining their tactics, while most organisations still rely on scheduled scans or annual pen tests. CTEM provides continuous visibility and validation, ensuring you're not caught off guard by rapidly emerging threats.
Your Attack Surface Is Always Changing
With the rise of cloud services, SaaS platforms, remote work, and shadow IT, your digital footprint is growing — and so is your risk. CTEM helps you discover and manage new assets and vulnerabilities in real time, reducing blind spots.
Not All Vulnerabilities Are Equal, Prioritise What Matters
CTEM focuses on business-contextual risk, helping you prioritise the exposures that pose real threats to your operations. This allows your security team to act faster and smarter, focusing resources where they’ll have the most impact.
Frequently Asked Questions about Continuous Threat Exposure Management
What is CTEM (Continuous Threat Exposure Management)?
CTEM is a proactive, ongoing cybersecurity approach that helps organisations identify, validate, prioritise, and reduce their exposure to cyber threats across their entire attack surface, aligning technical risks with business impact.
How is CTEM different from traditional vulnerability management?
Unlike traditional vulnerability scans or periodic pen tests, CTEM is continuous and risk-driven. It combines attack surface management, threat validation, and remediation support in an ongoing cycle, rather than relying on point-in-time assessments.
Why does my organisation need CTEM?
Modern threats evolve quickly, and attack surfaces are growing due to cloud, SaaS, and remote work. CTEM ensures you maintain real-time visibility into your vulnerabilities and can prioritise responses before attackers exploit them.
What are the main components of CTEM?
CTEM typically includes five key stages:
- Scoping
- Discovery
- Prioritisation
- Validation
- Mobilisation
Together, these create a continuous loop that improves security posture over time.
How often should CTEM activities be performed?
CTEM is designed to be ongoing, with continuous monitoring and validation. Activities like attack surface scanning and threat simulation occur regularly often daily or weekly depending on your risk profile and business needs.
Who benefits from CTEM in an organisation?
CTEM benefits security teams, IT leadership, compliance officers, and executive stakeholders by providing clear insight into cyber risk and aligning security actions with business priorities.
Does CTEM replace pen testing or vulnerability scanning?
No CTEM complements those practices. It enhances them by adding continuous visibility, prioritisation, and real-world validation to ensure that vulnerabilities are not just found, but understood and addressed effectively.
What tools or platforms are used in CTEM?
CTEM uses a combination of tools such as attack surface management platforms, threat intelligence feeds, exploit frameworks, validation tools, and remediation workflows. CyberGen integrates these into a tailored solution aligned with your organisation’s needs.
Discover the power of Continuous Threat Exposure Management (CTEM), a strategic, intelligence-driven approach to identifying, validating, and reducing cyber risk in real time across your entire attack surface.
Let's get protecting your business
Thank you for contacting us.
We will get back to you as soon as possible.
By submitting this form, you acknowledge that the information you provide will be processed in accordance with our Privacy Policy.
Please try again later.